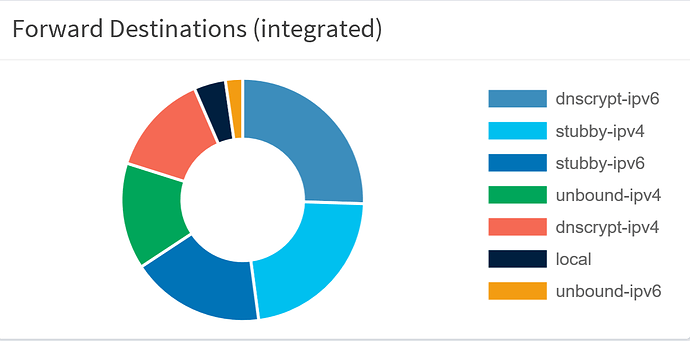
In this topic, I entered a screenshot of the different resolvers behind dnsmasq. As you can see and read, by using the hosts file, the name of each resolver is next to the graph, so I can exactly see witch resolver made dnsmasq happy. That is the goal, don't lose track of it, when proposing solutions!
I've finally got my provider to exchange my docsis v2 modem for a v3 (no firewall/router/wifi - I've got a pfsense box to handle that), and after some hick ups, I've got a Global Unique address on my pi (PD 56 on the WAN, 'track interface' on the LAN adapters.
In the topic, mentioned earlier, you can see I've assigned a unique IPv4 address to each of the different resolvers, e.g.
127.10.10.2 (unbound), 127.10.10.3 (stubby) and 127.10.10.4 (dnscrypt-proxy). This allowed me to modify the hosts file, as a result, the names are displayed with the graph. Raspian, my OS, seems to handle the routing between dnsmasq and the resolvers. If I traceroute the addresses of the resolvers, the request doesn't even leave the pi, example:
traceroute 127.10.10.4
traceroute to 127.10.10.4 (127.10.10.4), 30 hops max, 60 byte packets
1 127.10.10.4 (127.10.10.4) 0.124 ms 0.042 ms 0.037 ms
Reading up on IPv6, I found an article that claimes, you can safely use a Local Unique Address to achieve having a unique address for the IPv6 resolvers, so I configured fd12:3456:789a:1::15b0 (unbound), fd12:3456:789a:1::15b1 (stubby) and fd12:3456:789a:1::15b2 (dnscrypt-proxy)
The intention, again, is to add these addresses to the hosts file to identify the different resolvers.
However, traceroute and the firewall shows the pi is now attempting to find the resolvers, using a route, witch is of course NOT defined.
traceroute fd12:3456:789a:1::15b1
traceroute to fd12:3456:789a:1::15b1 (fd12:3456:789a:1::15b1), 30 hops max, 80 byte packets
1 2a02:1810:4d02:5602:20e:c4ff:fecf:f3cf (2a02:1810:4d02:5602:20e:c4ff:fecf:f3cf) 0.451 ms 0.300 ms 0.224 ms
2 * * *
3 * * *
The question (finally):
Is it possible (probably) to configure Raspbian to allow dnsmasq to find the resolvers on their respective IPv6 addresses, without having to revert to adding routes on the pfsense box, just like IPv4. This probably requires IPv6 routing configuration on the pi, but helas, I can't find any web page that indicates how to achieve this.
If at all possible, the solution should avoid to use the GUA of the pi, since, according to the pfsense NDP table, the address is NOT permanent.
Thanks
'edit'
found the article regarding the 'fd' IPv6 network, added the link
'/edit'